Xiting
Downloads
Here you can find current DOWNLOADS from OUR PORTFOLIO.
New Whitepaper

New whitepaper: SAP License Optimization from a Technical Perspective
In the era of SAP S/4HANA and “RISE with SAP,” license management has become a strategic discipline that directly affects compliance, security, and cost efficiency. With the shift from usage-based to authorization-based licensing, every assigned permission can influence overall license costs. This booklet outlines the technical foundations and optimization strategies that help organizations regain transparency, reduce risks, and establish sustainable, audit-proof license management with Xiting.
Whitepaper

Whitepaper: Reducing SAP Licensing Costs Through Targeted Analyses
This new white paper from Xiting provides companies with a practical guide for the efficient management and optimization of SAP licenses in the context of SAP S/4HANA. With the shift from transaction-based to authorization-based licensing models, companies face new challenges that require precise analysis and adjustment of authorizations.
Infografik
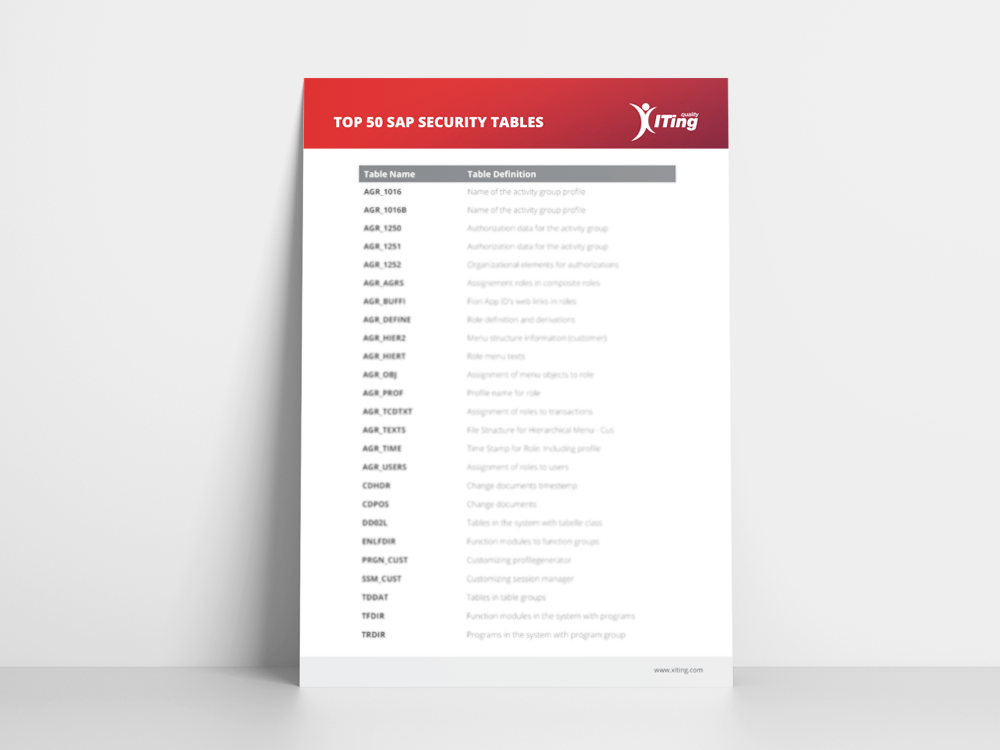
THE TOP 50 SAP SECURITY TABLES
In this download, you will find a comprehensive overview of the most important SAP Security tables. To access it, simply fill out the form shown on the right, download the table, and improve your workflow.
E-Book

SAP Cloud Identity Services: Best Practices & Use Cases
In our new e-book, we offer a concise overview of SAP Cloud Identity Services, including common use cases and Xiting best practices. Don’t let identity and access management slow you down—optimize your systems with SAP Cloud Identity Services!
E-Book

Connecting SAP Identity Authentication Service as a proxy to Azure AD using OpenID Connect
This e-book focuses on integrating the SAP Identity Authentication Service into your Azure tenant. We take a closer look at this topic, particularly with regard to OpenID Connect. Along the way, we cover some basics and explain the functionality and use cases of key standards such as SAML 2.0, OAuth 2.0, and OpenID Connect. In addition, we provide you with a configuration guide that offers deeper insights and supports you in setting up your SAP IAS and Azure tenant.
E-Book

SAP Security Hardening: Implement Security by Design und Zero Trust
In the age of cybercrime and constantly evolving vulnerabilities, implementing a Zero Trust strategy and Security by Design is crucial to effectively harden any IT system, including SAP. This whitepaper outlines the key points to help you get started.
Infographic

SAP Fiori Apps vs. Classic SAP Applications
Customers who have chosen SAP Fiori as their primary front-end technology can confirm from their own experience that providing apps in the Fiori Launchpad is more time-consuming and complex than authorizing transactions in the SAP GUI. For customers who have yet to make this transition, we aim to offer explanations in this article as to why this is the case.
Booklet

Xiting Security Solutions Booklet
This brochure provides a comprehensive overview of all Xiting security solutions and services. We present a range of practical use cases covered by XAMS, XSP, and other Xiting solutions, showing you how to address your individual challenges in the SAP security environment.
Freeware

XAMS Freeware Tools
Take advantage of our XAMS freeware tools, which are an integral part of XAMS. With the User Locking and RFC Stocktaker tools, we offer you two applications that can significantly enhance the security of your SAP systems. Get our tools and experience the Xiting Authorizations Management Suite (XAMS) for yourself.
E-Book

SAP S/4HANA – The Future of the SAP Product Portfolio
Alexander Sambill, SAP Security Consultant at Xiting, has created a comprehensive overview on the topics of SAP S/4HANA, authorization migrations, SAP HANA, and SAP Fiori. Download this e-book to get an overview of the new 4th generation product line and its features in the authorization context.
Booklet

SAP Identity Management – Solutions & Services
With this new booklet, you will get an introduction to the world of SAP Identity Management. Learn more about the benefits of SAP IDM and our specific services. You will also get to know the new products, Xiting Central Workflows & Xiting Fiori UI for SAP IDM, in more detail.