The Security Audit Log – What should be considered with an SAP Audit?
The background
Increasing demands on IT security and data protection require ever stronger safeguards in IT systems. SAP is a crucial component for every company in which it is used. SAP systems have highly sensitive data and the responsibility for this data lies with the company itself. One way to additionally secure the SAP system is to activate the Security Audit Log or SAL for short. Auditors use this logging function and evaluate it accordingly. It is essential for auditors because it allows them to check the security of your system. We will show you what the SAP standard tool can do and how our software solution Xiting Authorizations Management Suite (XAMS) supports you in maintaining your SAL settings according to best practice recommendations.
What is the security audit log?
The Security Audit Log is a standard SAP tool and is used to record security-relevant information with which you can track and log a series of events. This is especially true for dialog user IDs with extensive permissions. If the configuration is not active or has an unclean state, there is a risk in the form of security breaches due to malicious intent or misuse. The possibility to track the perpetrator is then only possible to a limited extent. For example, a user can try systematically to try another user’s password. If the logon attempts succeed, he can gain access to elevated authorizations and misuse the system. Users with extensive permissions should therefore always be recorded. Such real-time audit log events can be logged and stored with the SAL audit log file which could include system log data, IP address, SAP instance, ERP application server, ABAP programs, RFC calls, function calls, security events, and change documents depending on the tables being logged.
Examples of possible events for recording are:
- Recording of security-related changes to the SAP system environment (e.g., changes to user master records).
- Identification of information that provides more transparency (e.g., successful and unsuccessful login attempts and calls).
- Determination of information that serves the traceability of a series of events (e.g., successful or unsuccessful transaction starts).
Hint:
As of SAP NetWeaver 7.50, there are new transactions for SAL (SAP Note 2191612). Transaction code RSAU_CONFIG is used to set up the Security Audit Log configuration. Previously, transaction SM19 was used. In addition, there is the new display transaction for configuring RSAU_CONFIG_SHOW. As soon as you have performed changing access for the first time in transaction RSAU_CONFIG, you can only use the SM19 for display purposes. Since SAP Basis Version 7.55, you can once again use both transaction SM19 for configuration maintenance and SM20 for evaluation.
Instead of the SM20, there is now the transaction RSAU_READ_LOG to analyze the SAL.
HOW SHOULD I CONFIGURE MY SAL? WHICH USERS NEED TO BE RECORDED?
There are over 90 events that can be activated in the SAL. It is not uncommon for SAP security and SAP Basis teams to want to activate all event types (audit classes) at the same time. However, this comes at the expense of the storage space. By default, the recorded log entries are stored in the file system and not in the database. Thus, they have no direct influence on the performance of the system. The focus of the base teams is therefore on the storage requirements. Logs are not automatically archived, and when storage capacity is reached, events are no longer recorded. Depending on which event types are activated, the data volume can change significantly. Our recommendations are based on the best practice of the DSAG Test Guide. The SAL settings are part of the DSAG (German-speaking SAP User Group) test program for monitoring the effectiveness of access protection.
The configuration for the SAP Security Audit Log may only be activated and adapted in the production system by system administrators.
HOW IS THE SAL EVALUATED?
The evaluation and reading of the Security Audit Log take place via transaction SM20 or RSAU_READ_LOG. There can be restricted according to various criteria. The evaluation should only be carried out in the production system by a limited group of people who are responsible for the task of monitoring and evaluating the events.
MONITORING THE SAL WITH THE XAMS
We would now like to show you how you can permanently monitor your SAL settings with the Security Architect, which is a module of Xiting’s own SAP security solution Xiting Authorizations Management Suite (XAMS for short). With the Security Architect, you can create a best-practice security concept and continuously monitor your SAP systems for compliance problems. In combination with the Solution Manager, you can manage your global SAP security concepts and compare the correct parameterization with connected systems. In addition, numerous ICS check functions can be carried out in the Security Architect by means of a check mode. With the help of this check mode, you can also compare check functions for the settings of the Security Audit Log. You can compare Customizing directly against the status in the system. This can be carried out locally for one system or centrally (e.g., via the Solution Manager) for all connected systems at any time.
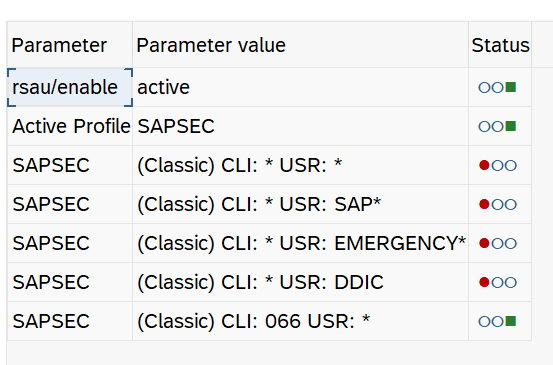
You can check whether an active profile is stored in the Security Audit Log and whether it has at least one criterion. It is also checked whether the profile parameter rsau/enable is active. A further check helps you to compare the settings in SAL with the minimum settings within the defined Customizing.
The checks are displayed in a user-friendly display. Based on the traffic light system (red-green) you can see the status of your test directly. In our case in Figure 1, the settings in the Security Audit Log differ from the minimum settings within Customizing in the two systems S4D and S4T.
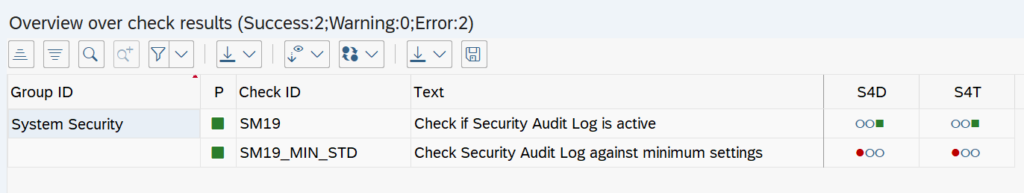
Double-clicking on the red light opens the window in Figure 2 and shows us the status of the settings that deviate from Customizing.
You can schedule the ICS check checks periodically. You also have the option to call up results from old exams and compare them with the current ones. Thus, you always have an overview of your progress.
Result
Enabling the Security Audit Log is a crucial step towards security as it provides detailed information about the audit reports. It is part of every security analysis by auditors. The advantages far outweigh the low setting effort and enable long-term data access to the set records. The Security Architect of the XAMS software solution supports you in checking the security status of your SAP landscape against your defined Customizing.
If you have any questions about the Security Audit Log regarding logging, log files, log events, and about SAP authorizations, S/4HANA, and RFC, our experts from the Authorization Team at Xiting will be happy to help you.